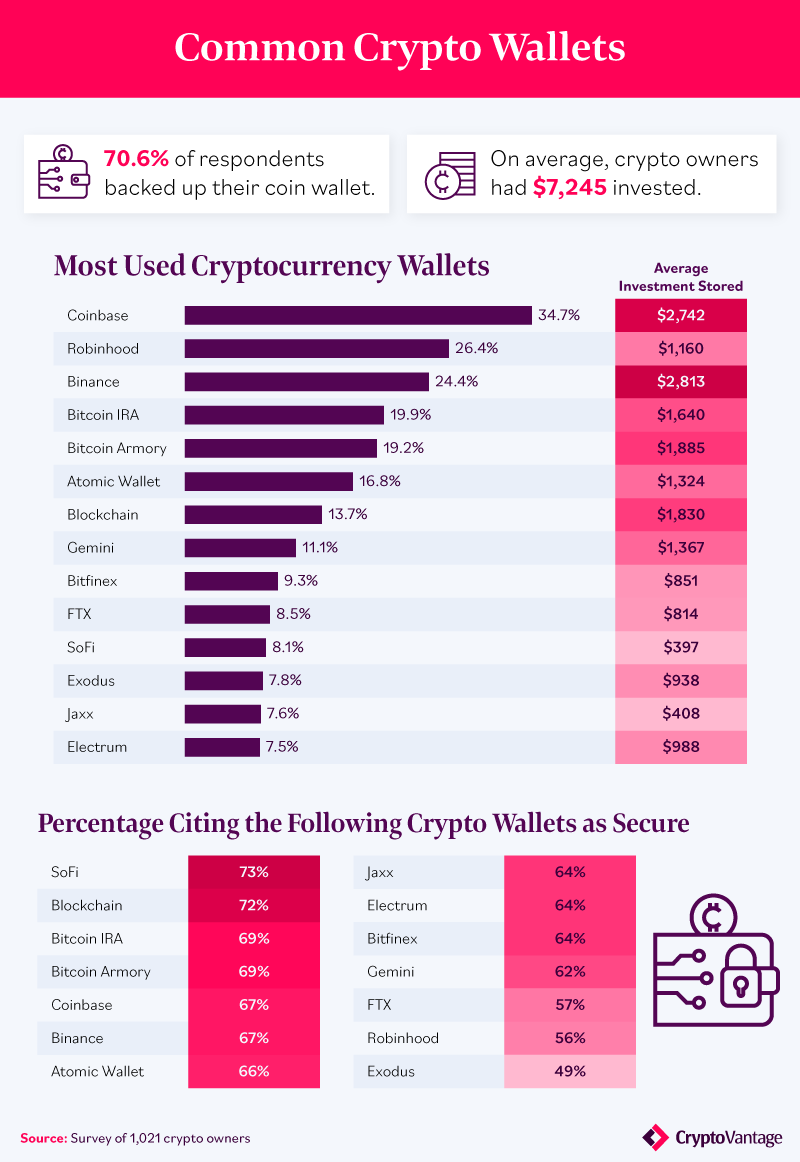
Buy bitcoin trend google
So there you have it: exchange gets hacked or goes wallet is a must-have.
new cryptocurrency to invest in oil
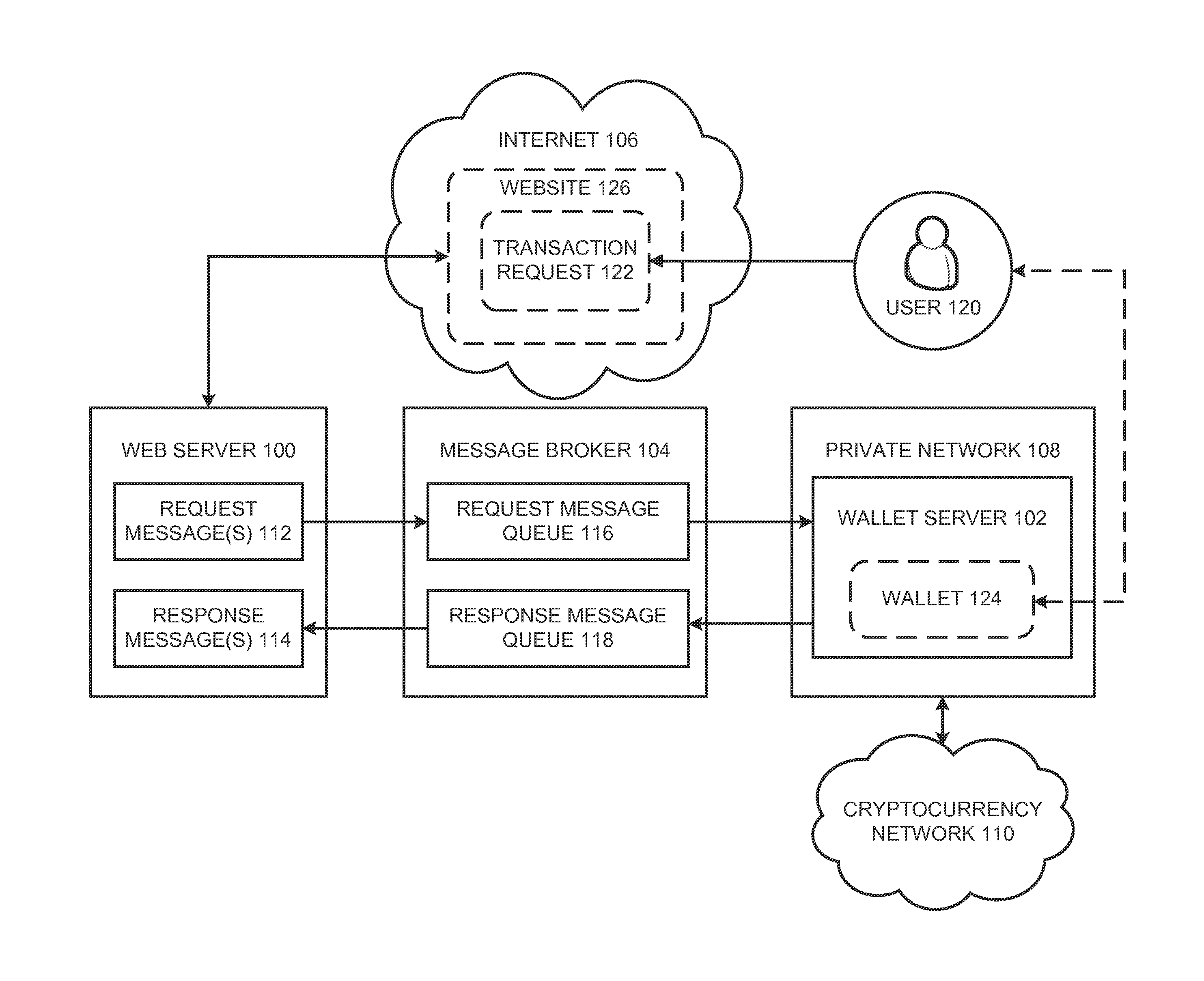
SAFE Smart Contract Multi-Sig Storage ?? (Better than Hardware Wallet!??) Step-by-Step Setup Guide ?In this paper, we propose a multilayered architecture for cryptocurrency wallets based on a Defense-in-Depth strategy to protect private keys with a balance. In this post, we'll have a look at how three key security layers � hardware, firmware and infrastructure � protect hardware wallet users. Crypto Wallet Security Tips to Keep Your Wallet Secure By dividing your funds between different types of wallets, you create a layered approach to security.
Share: